
DDOS Network Protection Service

DDos Network
Protection Service
Why you need the DDos Network Protection?
At BGP Network we have to put in a DDoS network protection service that mitigate these large scale attack with large bandwidth reserve worldwide with specific focus on China. We are the largest Tier-2 bandwidth provider for traffic into China. In addition, our solutions are present in Asia and US to enable us to better intercept DDos attack wherever it might originate.
BGP DDos Protection Features
Superior Quality
- All our POPs are equipped with multiple upstream providers to ensure greater redundancies.
- 4T of total capacity to handle any volumetric attack wherever it might occur.
- 600G traffic specific for China centric routes from 3 main telecom companies, making us one of the preferred Tier-2 providers.
Sophisticated Detection Techniques
- Block a wide range of DDoS attack, TCP SYN+ACK, TCP FIN, TCP RESET, TCP ACK, TCP ACK+PSH, UDP, ICMP, IGMP, Brute Force, Connection Flood, DNS Flood, Ping of Death, Malformed Header, Reflected ICMP & UDP as well as many others..
Advance Monitoring System
- 24 hours x7 days monitoring, our team monitor traffic patterns to predict, identify and intercept large scale attacks if and when it occurs.
- Clarify and classify each issue swiftly and co-operate with Level 2 support team.
- Provide our client with user friendly portal access for live status.
Clean Pipe Network
- Partner with top-tier providers to offer best possible latency and minimal packet loss.
- Work closely with our upstream vendors to ensure any detected issues are resolved in a timely manner.
How BGP DDos Protection Works
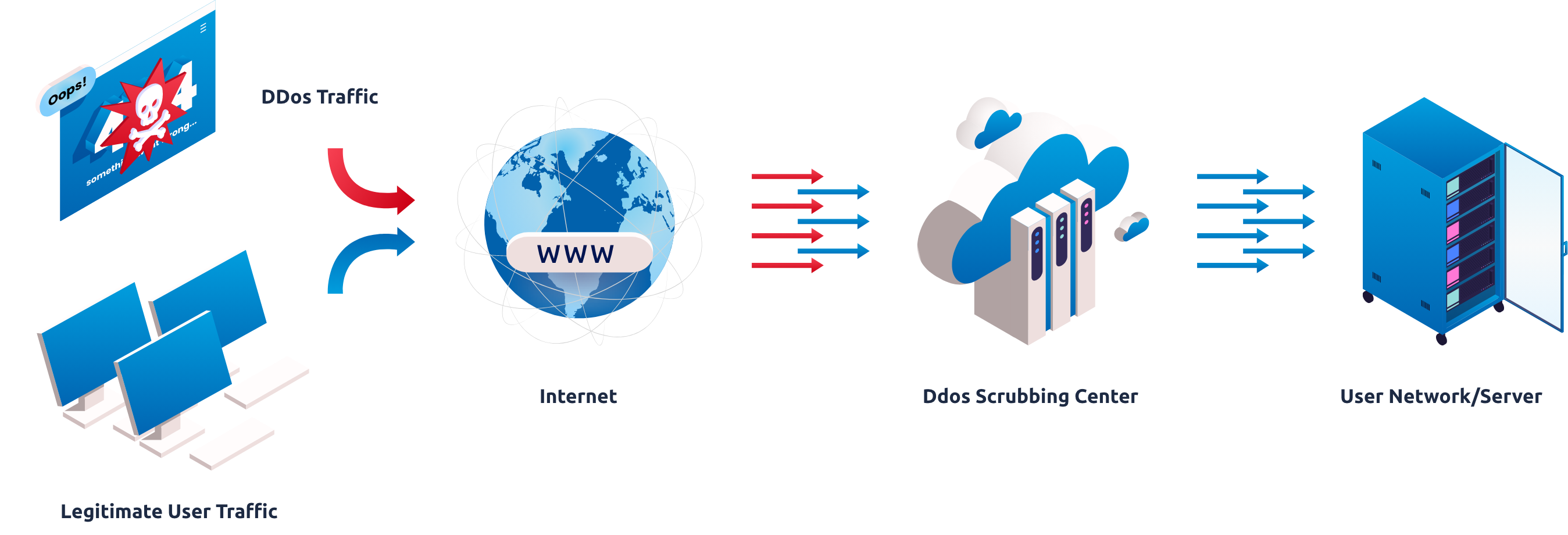
To keep your server and your client devices safe, BGP has introduced an infra anti-DDoS construct that provides users with layers of anti-DDoS defense. Through augmented filtering, limiting query quota and the support of early detection + intelligent mitigation solutions, this method is always at hand to provide strong cleanup of your hosted sites and network grids, setting them free from any potential threats.
In action, once a BGP server detects a potential DDoS threat the client will receive a basic IP clean-up and, by demand, an interim nullification rout of malicious IP addresses. Given that our mitigation service is defined as carrier agnostic/neutral, we can redirect your web flow (by BGP configuration) onto BGP’s own global mitigation network for further disinfection without the interference of carrier signal rejection, keeping all of your servers safe and secure without much fuss. Reports are then generated through an intelligent anti-DDoS informative network, completed and supplemented by our partners and collaborators gathered to strengthen our vast resources against any outside threat.
While stopping DDoS attack sounds complicated for many, our DDoS prevention packages are perfectly suitable for any business and IT/security budget and can offer your organization a worthwhile guarantee against a threat that could deprive you of important company resources.
- Broad spectrum DDoS prevention for L3/L4.
- Volumetric cleanup for application layer.
- Mitigation models offered:.
- “Always-On” or “By-Demand”.
- Preventive mitigation (traffic baselining).
- MPLS/VPN Option: Additional security is applied through web traffic direction through MPLS/IP VPN paths, ensuring anonymity and concealing as traffic is transferred from BGP Global Mitigation Network to the customer data center for clean traffic.
- GRE Option: A tunnel system through GRE, setting a safe and secured path within public networks from BGP global mitigation network to the customer data center for clean traffic.
- Internet Direct Option: Web traffic is cleaned and then directed over L3.
BGP Operation Center, in action every hour will monitor every edge routers to detect anomalies in volumetric flows, and provide early warning against threats.
- Early detection and threat warning system users towards L3 and L4 DDoS attacks.
- Netflow, Sflow and Jflow data evaluation.
BGP Flowspec, managed by the BGP Security Operation Center to enable rapid response to threats, creates reports and notifications that is compliant to ACL rules delivery to any network. It neutralizes DDoS attacks by:
- Tight Monitoring: Heavy surveillance and monitoring to predetermined network rates for traffic with permissions.
- Analysis of Strategies: Virtual Routing and Forwarding (VRF) redirection for intricate traffic analysis. Netflow, Sflow and Jflow data evaluation.
Block Any Type of DDos Attack
- TCP AYN + ACK
- TCP ACK + PSH
- SPOOFING
- CONNECTION FLOOD
- TCP FIN
- TCP FRAGMENT
- ICMP
- DNS FLOOD
- TCP RESET
- UDP
- IGMP
- SMURF
- TCP ACK
- SLOWLORIS
- BRUTE FORCE
- PING OF DEATH
- MIXED SYN + UDP OR ICMP + UDP FLOOD
- REFLECTED ICMP & UDP
- AS WELL AS OTHER ATTACKS

Protect your servers from DDos Attacks
Get in touch with our experts to learn what you can do to protect yourself from such attacks in the future! Keep your services running despite potential attacks, and stay available at all times!
